How to change host name in CentOS / REHL
In CentOS /RHEL 7, we have 3 host names:
The easier solution might be adding your host name and its IP to the DNS server.
1. Static host name a.k.a. kernel host name, is initialized from /etc/hostname file at boot time so to change it you can simply enter the new name in this file.
2. Transient host name, is a temporary host name assigned by a DHCP server or such a program.
Note: static and transient host names follow the same rules as Internet domain FQDNs so for example you can not use space character in these host names.
3. Pretty host name, is a free-style form name that you can put on the computer such as "Behnam's Server"
hostnamectl is a new command in CentOS 7 which allows you to view or change the host name. To change all 3 kind of host names at the same time, enter:
# hostnamectl set-hostname www.pournader.com
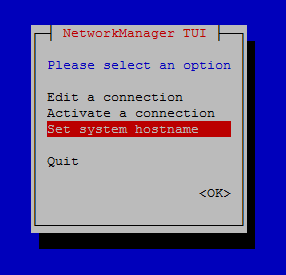
Another way to change the host name is using nmcli or nmtui:
#nmtui
And you will face such an interactive and easy-to-use text user interface:
Note: You do not have to reboot the machine to activate permanent host name change. Just log out and log in again to see the new host name in the prompt.
If you want to change just one type of the host name simply specify the type of host name as below:
# hostnamectl --static set-hostname www.pournader.com
To clear a particular host name and let it revert to its default:
# hostnamectl --transient set-hostname ""
If you run version 6 or 5 of CentOS / RHEL, steps are totally different. You should do the following:
a. Use hostname command to change the host name:
# hostname www.pournader.com
b. Open /etc/sysconfig/network and edit HOSTNAME value to what you want to put on the host.
c. Open /etc/hosts and add the appropriate line. Actually this step is not necessary. Also you can do in CentOS / RHEL 7 if you want.
d. restart network service:
# service network restart
The easier solution might be adding your host name and its IP to the DNS server.